The Human Story
For nearly ten years I’ve been working with a small family-run online store — one of those “mom & pop” operations where every order matters and every checkout is hard-earned.
This year, something changed.
Thousands of fake checkout attempts started flooding in. Orders that never converted, emails that never delivered, and a quiet worry growing behind the scenes.
It turned out the site was being used as a playground by fraudsters: testing stolen credit cards to see which ones worked, before using them for much larger attacks elsewhere.
In just a few weeks, the business recorded 4,337 failed orders — all non-legitimate.
That’s when I stepped in. I carved out a day in my calendar, built a custom solution — and put a stop to the nonsense.
The Technical Reality
We tried everything: additional server security, WordPress and WooCommerce updates, firewalls, brute-force protections, malware tools.
Yet the problem didn’t stop. Why?
Because the checkout process allowed the payment gateways (like PayPal Express) to load before any meaningful email verification — meaning bots, fake emails and stolen cards could get through the form, click payment, and test the system.
In other words: transactions were being attempted under false identities, purely to probe which cards succeeded.
That’s when I realised the answer wasn’t just more “security”. It was a deliberate road-block — placed before payments even appear.
The Moment of Clarity
I built the “OTP-Gate” solution for the store in one focused session.
Here’s how it works:
- Customer enters billing email.
- System sends a six-digit OTP (one-time code) to that email.
- Until the code is confirmed, payment options are removed — PayPal, Stripe, everything is removed.
- Once verified, payment methods unlock and the checkout continues normally.
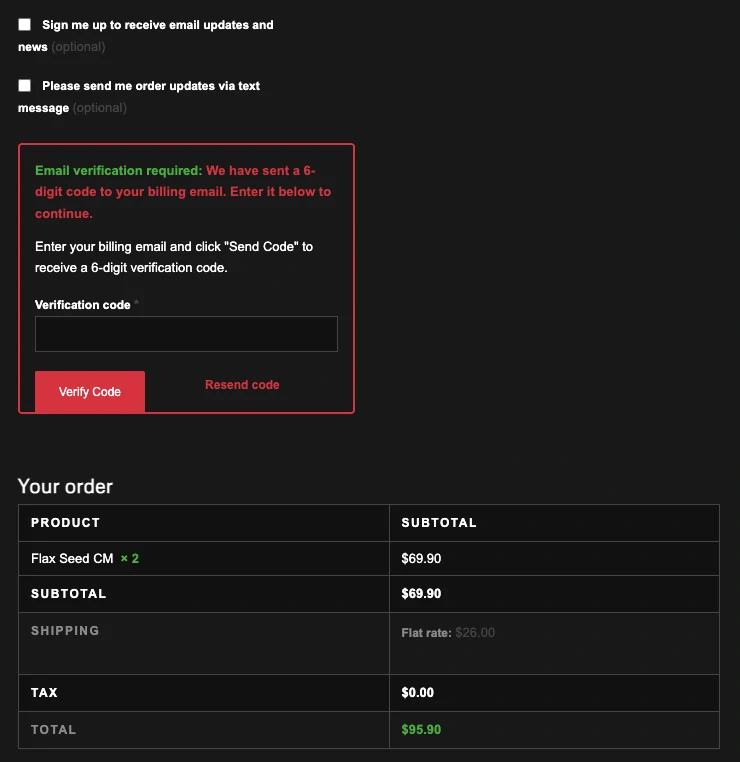
Suddenly, the store wasn’t just waiting for fraud to hit — it was pre-filtering it.
And overnight, the fake orders dropped to zero.
The Bigger Problem Nobody Talks About
My client’s experience is far from unique.
Across small WooCommerce stores — especially those using PayPal Express or fast “buy now” buttons — fraudsters are quietly testing stolen cards — picking off the weaker children in the e-commerce ecosystem.
These stores aren’t being hacked; they're being abused.
And each failed order still costs:
- Bandwidth
- Support staff time
- Email processing
- Lost revenue potential
Worst of all, many owners don’t even know it’s happening — they just see “failed payment” or “abandoned cart” numbers rising.
The “OTP Gate” Solution
Here’s what the Villiers | Vision | Works solution delivers:
- Verifies billing email with an OTP before any payment gateway appears.
- Removes PayPal, credit-card buttons, express checkouts until verification succeeds.
- Built with secure HMAC signature, Node.js / Next.js API, optional Redis / Vercel KV fallback.
- Seamless for real customers — invisible friction for legitimate orders, major pain for fraud bots.
- Designed specifically for small-to-midsize WooCommerce stores that aren’t enterprise-funded, yet still vulnerable.
The Results
Immediate Impact:
- Zero fraudulent checkout attempts since implementation
- Legitimate customer conversion improved — because trustworthy process inspires confidence
- Owner regained control, stopped anomaly emails, and focused on genuine growth instead of cleanup
It wasn’t a patch. It was a turning point.
The Human Takeaway
I didn’t build this because I had to — I built it because I wanted to protect a world where small businesses get the same safeguards big brands take for granted.
If one day of focused development can stop a year’s worth of losses, then it’s absolutely worth doing.
At Villiers | Vision | Works we believe in tech that works for people — not just platforms.
Your ideas deserve protection.
Technical Implementation Highlights
Architecture:
Key Technologies:
- WooCommerce Hooks & Filters for checkout process integration
- HMAC Signature Verification for secure OTP generation
- Node.js / Next.js API for email delivery
- Redis / Vercel KV for OTP storage and expiration
- Custom JavaScript for frontend UX
Security Features:
- Time-limited OTP codes (e.g., 5-minute expiration)
- Rate limiting on OTP requests
- HMAC-based signature validation
- Secure email transmission
- No payment gateway exposure until verified
Is Your Store Vulnerable?
If you run a WooCommerce store and you’re seeing odd patterns, failed payments, rising support tickets — this could be your hidden vulnerability.
Warning Signs:
- Increasing “failed payment” or “abandoned cart” rates
- Fake email addresses in order history
- Multiple failed transactions from similar IPs/patterns
- Support tickets about “orders I never placed”
- Payment gateway test charges that never complete
Let’s Talk
I’ll walk you through how we can implement the same OTP Gate (or a tailored version) for your store.
Reach out to:
Anton de Villiers — Founder, Villiers | Vision | Works (PTY) LTD
📧 info@vvwsoftware.com | 📞 +27 87 150 9305
Website: vvwsoftware.com
About the Author
Anton de Villiers is the founder of Villiers | Vision | Works — a South African-based consultancy specialising in secure, high-impact e-commerce and custom web solutions. With over 25 years of experience in IT and over a decade of WooCommerce expertise, Anton has built and protected online stores for businesses around the world.
